文章介绍:VyOS 配置 OpenVPN 服务端模式,iKuai 软路由 OpenVPN 客户端拨号连接,实现简单组网,采用账号密码加证书认证方式实现。
一、VyOS
1.1、VyOS镜像
1.2、VyOS安装
1.3、VyOS基础
二、VyOS配置OpenVPN
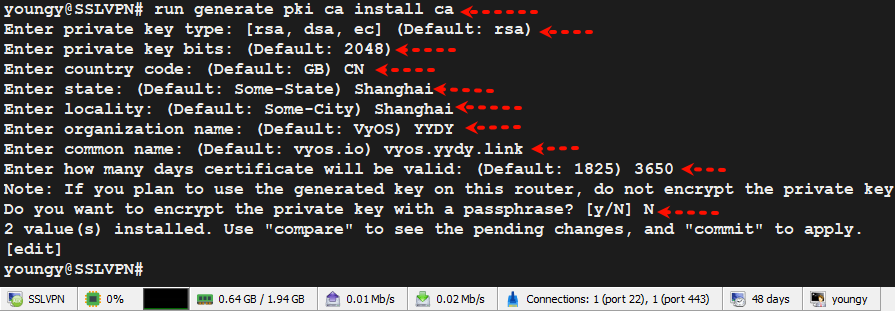
2.1、生成ca证书
run generate pki ca install ca
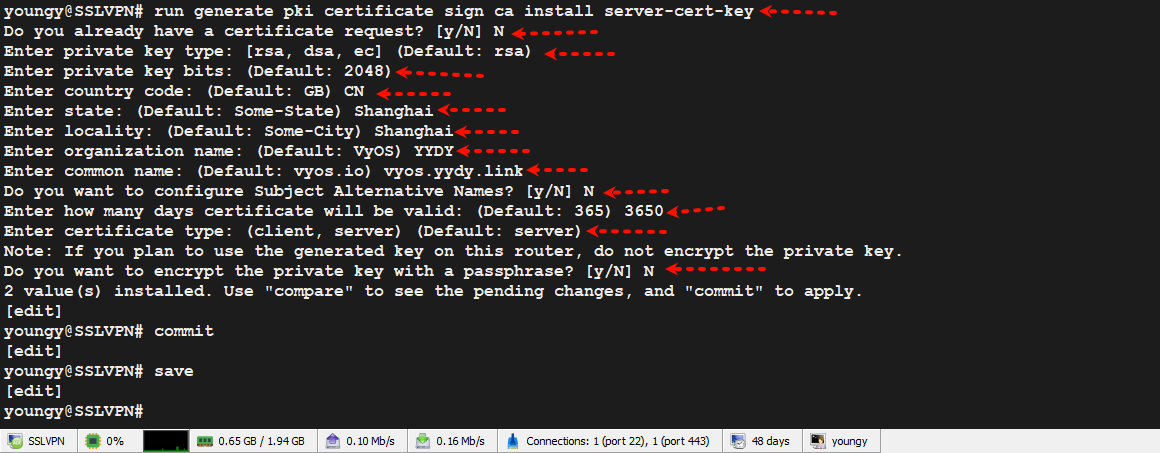
2.2、生成服务端证书和密钥
run generate pki certificate sign ca install server-cert-key
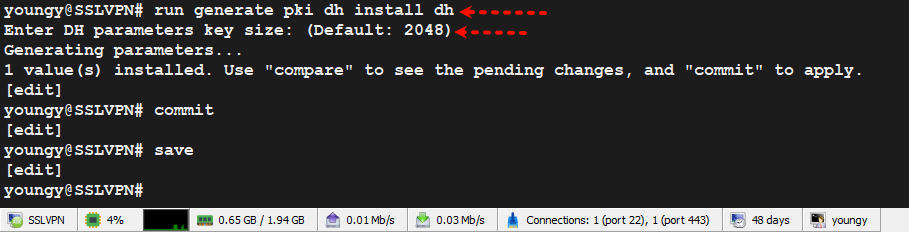
2.3、生成客户端证书和密钥
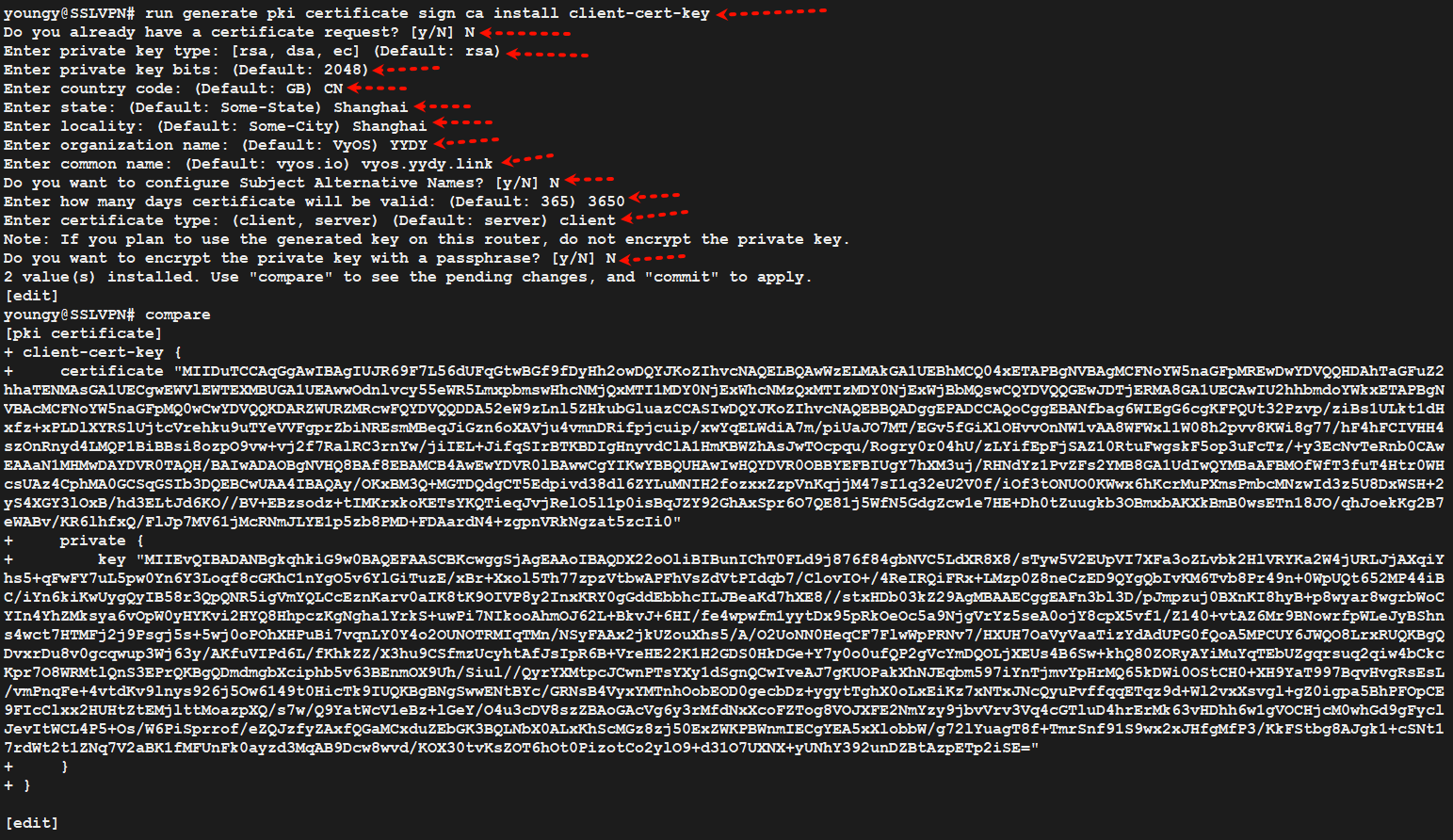
run generate pki certificate sign ca install client-cert-key
2.4、创建checkpsw.sh
sudo nano /config/auth/checkpsw.sh
#!/bin/sh
###########################################################
# checkpsw.sh (C) 2004 Mathias Sundman <[email protected]>
#
# This script will authenticate OpenVPN users against
# a plain text file. The passfile should simply contain
# one row per user with the username first followed by
# one or more space(s) or tab(s) and then the password.
###########################################################
PASSFILE="/config/auth/openvpn_user_passwd.txt"
LOG_FILE="/config/auth/openvpn.log"
TIME_STAMP=`date "+%Y-%m-%d %T"`
if [ ! -r "${PASSFILE}" ]; then
echo "${TIME_STAMP}: Could not open password file \"${PASSFILE}\" for reading." >> ${LOG_FILE}
exit 1
fi
CORRECT_PASSWORD=`awk '!/^;/&&!/^#/&&$1=="'${username}'"{print $2;exit}' ${PASSFILE}`
if [ "${CORRECT_PASSWORD}" = "" ]; then
echo "${TIME_STAMP}: User does not exist: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
fi
if [ "${password}" = "${CORRECT_PASSWORD}" ]; then
echo "${TIME_STAMP}: Successful authentication: username=\"${username}\"." >> ${LOG_FILE}
exit 0
fi
echo "${TIME_STAMP}: Incorrect password: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
2.5、赋权checkpsw.sh
sudo chmod +x /config/auth/checkpsw.sh
2.6、创建密码本
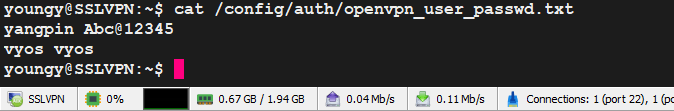
sudo nano /config/auth/openvpn_user_passwd.txt
2.7、赋权密码本
sudo chmod 664 /config/auth/openvpn_user_passwd.txt
2.8、创建拨号日志文件
sudo touch /config/auth/openvpn.log
2.9、OpenVPN接口
set interfaces openvpn vtun11996 description 'OpenVPN-Server'
set interfaces openvpn vtun11996 local-host '123.123.123.123'
set interfaces openvpn vtun11996 local-port '11996'
set interfaces openvpn vtun11996 mode 'server'
set interfaces openvpn vtun11996 openvpn-option '--script-security 3'
set interfaces openvpn vtun11996 openvpn-option '--persist-key'
set interfaces openvpn vtun11996 openvpn-option '--duplicate-cn'
set interfaces openvpn vtun11996 openvpn-option '--auth-user-pass-verify /config/auth/checkpsw.sh via-env'
set interfaces openvpn vtun11996 openvpn-option '--username-as-common-name'
set interfaces openvpn vtun11996 openvpn-option '--cipher AES-256-GCM'
set interfaces openvpn vtun11996 openvpn-option '--tun-mtu 1500'
set interfaces openvpn vtun11996 openvpn-option '--mssfix 1300'
set interfaces openvpn vtun11996 persistent-tunnel
set interfaces openvpn vtun11996 protocol 'udp'
set interfaces openvpn vtun11996 server client ikuai ip '100.64.168.2'
set interfaces openvpn vtun11996 server client ikuai push-route '192.168.65.0/24'
set interfaces openvpn vtun11996 server client-ip-pool start '100.64.168.2'
set interfaces openvpn vtun11996 server client-ip-pool stop '100.64.168.254'
set interfaces openvpn vtun11996 server client-ip-pool subnet-mask '255.255.255.0'
set interfaces openvpn vtun11996 server max-connections '250'
set interfaces openvpn vtun11996 server subnet '100.64.168.0/24'
set interfaces openvpn vtun11996 server topology 'subnet'
set interfaces openvpn vtun11996 tls ca-certificate 'ca'
set interfaces openvpn vtun11996 tls certificate 'server-cert-key'
set interfaces openvpn vtun11996 use-lzo-compression
set interfaces openvpn vtun11996 description 'OpenVPN-Server':为接口添加描述,标识其为OpenVPN服务端set interfaces openvpn vtun11996 local-host '123.123.123.123':绑定服务端监听的本地IP地址set interfaces openvpn vtun11996 local-port '11996':设置服务端监听的UDP端口set interfaces openvpn vtun11996 mode 'server':定义接口工作模式为服务端set interfaces openvpn vtun11996 openvpn-option '--script-security 3':设置脚本安全级别为3,允许执行带外部调用的脚本set interfaces openvpn vtun11996 openvpn-option '--persist-key':启用密钥持久化,重连时无需重新读取私钥set interfaces openvpn vtun11996 openvpn-option '--duplicate-cn':允许相同通用名称的客户端同时连接set interfaces openvpn vtun11996 openvpn-option '--auth-user-pass-verify /config/auth/checkpsw.sh via-env':通过指定脚本验证客户端账号密码,信息通过环境变量传递set interfaces openvpn vtun11996 openvpn-option '--username-as-common-name':将客户端用户名作为TLS认证的通用名称set interfaces openvpn vtun11996 openvpn-option '--cipher AES-256-GCM':指定数据通道加密算法为AES-256-GCMset interfaces openvpn vtun11996 openvpn-option '--tun-mtu 1500':设置TUN设备的MTU为1500字节set interfaces openvpn vtun11996 openvpn-option '--mssfix 1300':限制TCP最大分段大小为1300字节,避免分片set interfaces openvpn vtun11996 persistent-tunnel:启用隧道持久化,空闲时不主动断开连接set interfaces openvpn vtun11996 protocol 'udp':使用UDP协议传输VPN数据set interfaces openvpn vtun11996 server client ikuai ip '100.64.168.2':为标识为ikuai的客户端分配固定IPset interfaces openvpn vtun11996 server client ikuai push-route '192.168.65.0/24':向ikuai客户端推送192.168.65.0/24网段的路由set interfaces openvpn vtun11996 server client-ip-pool start '100.64.168.2':定义客户端动态IP池的起始地址set interfaces openvpn vtun11996 server client-ip-pool stop '100.64.168.254':定义客户端动态IP池的结束地址set interfaces openvpn vtun11996 server client-ip-pool subnet-mask '255.255.255.0':指定IP池的子网掩码set interfaces openvpn vtun11996 server max-connections '250':限制最大并发客户端连接数为250set interfaces openvpn vtun11996 server subnet '100.64.168.0/24':定义VPN客户端所属的统一子网set interfaces openvpn vtun11996 server topology 'subnet':配置VPN网络拓扑为子网模式,客户端共处同一子网set interfaces openvpn vtun11996 tls ca-certificate 'ca':指定用于TLS认证的根证书set interfaces openvpn vtun11996 tls certificate 'server-cert-key':指定服务端的TLS证书和私钥set interfaces openvpn vtun11996 use-lzo-compression:启用LZO数据压缩,优化传输效率
三、iKuai配置OpenVPN
3.1、CA证书获取
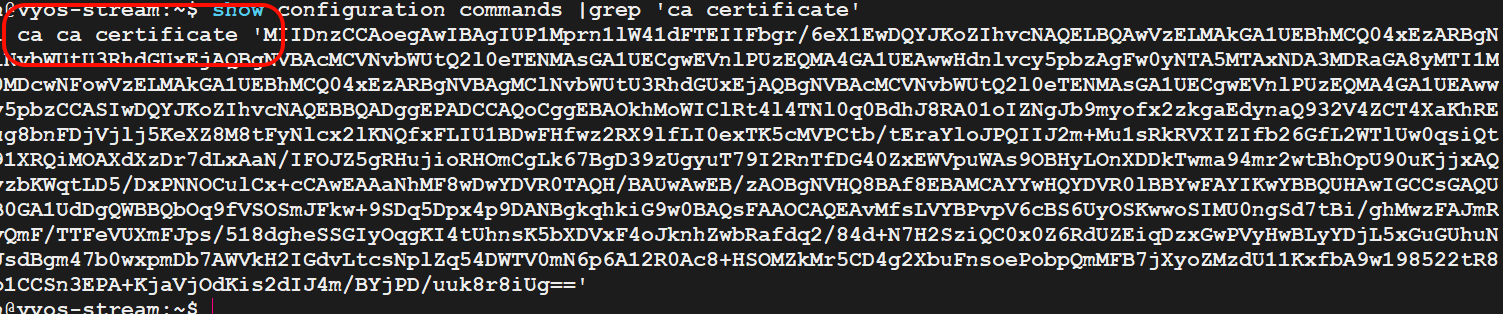
show configuration commands |grep 'ca certificate'
3.2、客户端证书获取
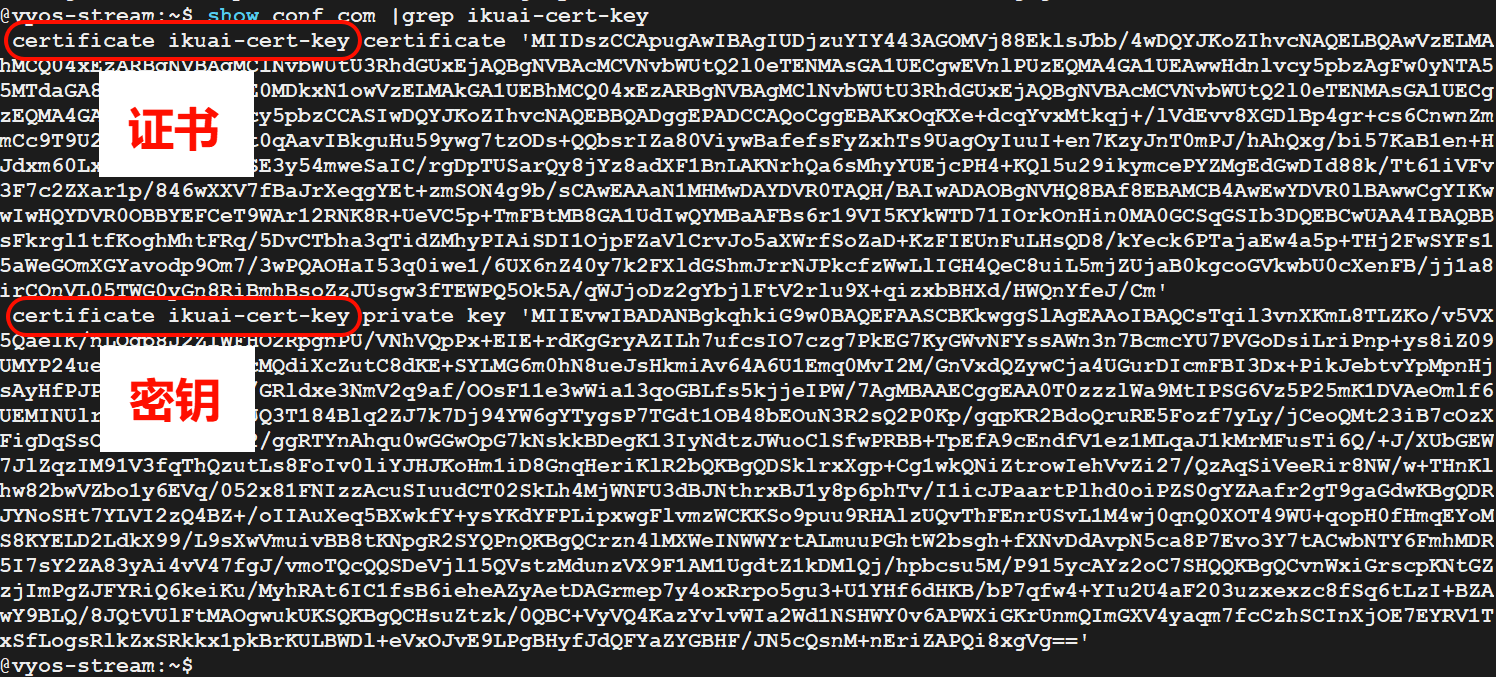
show conf com |grep client-cert-key
3.3、iKuai填写CA证书模板
-----BEGIN CERTIFICATE-----
这里填刚刚从vyos里面show出来的内容,只需要单引号里面的内容。
-----END CERTIFICATE-----
3.4、iKuai填写客户端证书模板
-----BEGIN CERTIFICATE-----
这里填刚刚从vyos里面show出来的内容,只需要单引号里面的内容。
-----END CERTIFICATE-----
3.5、iKuai填写客户端私钥模板
-----BEGIN RSA PRIVATE KEY-----
这里填刚刚从vyos里面show出来的内容,只需要单引号里面的内容。
-----END RSA PRIVATE KEY-----
3.6、iKuai完整配置
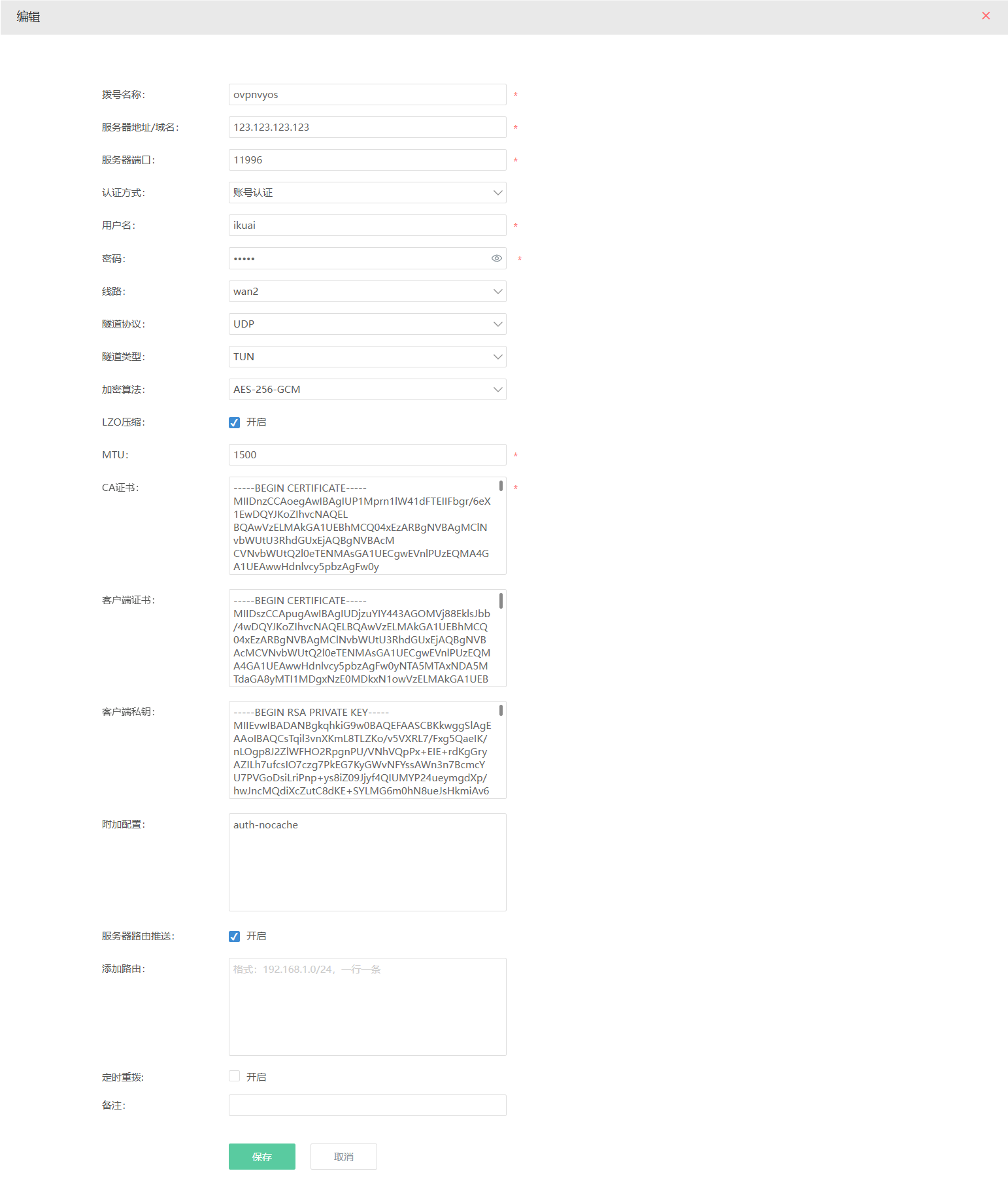
四、连接状态查询
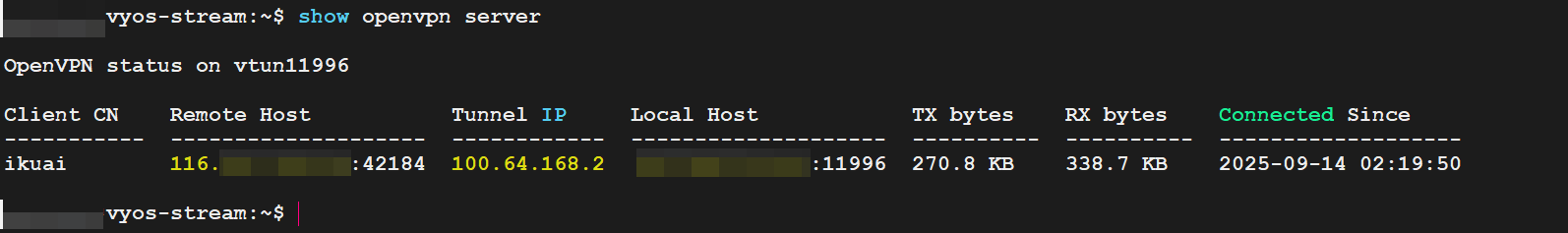
4.1、VyOS查看
show openvpn server
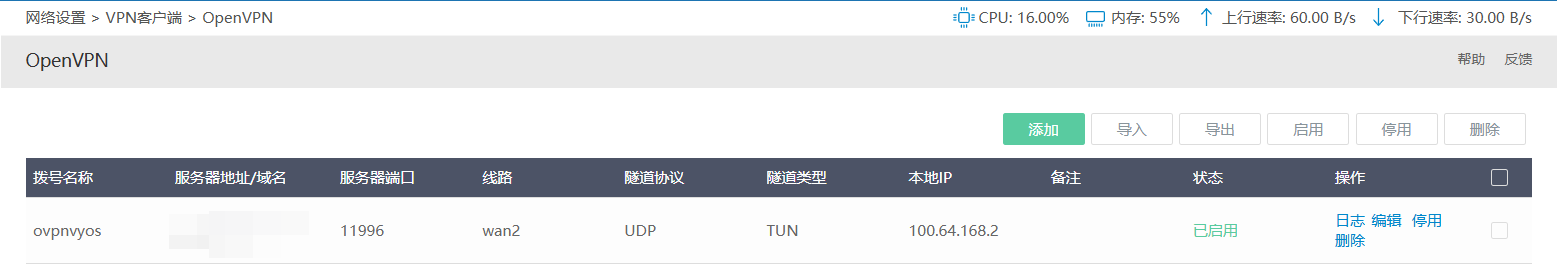
4.2、iKuai查看
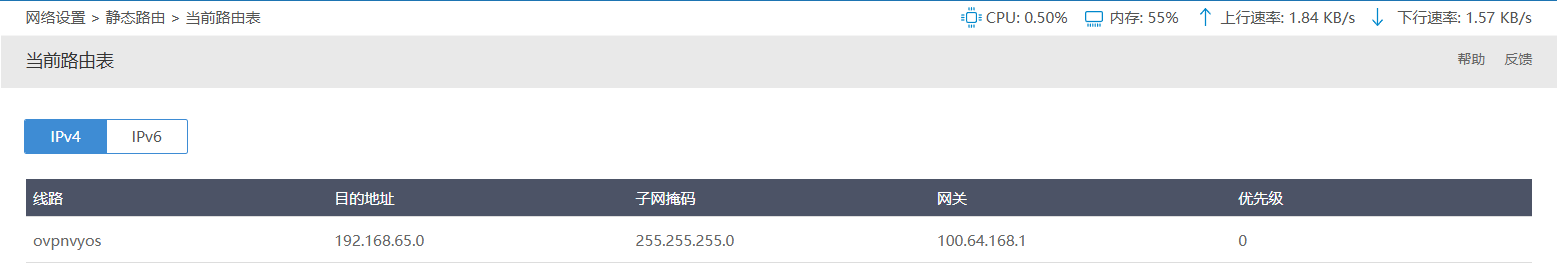
4.3、iKuai路由表查看
4.4、爱快traceroute测试